Today I present to you a very useful tool that I would like to share with you. If you work in information technology or dabble around with it, this tool may be of great use to you. Inspired by http://www.hackfromacave.net/katana/, I have made my own multi-booting USB flash drive. This is not a replacement for Katana but just merely an alternative. I present to you: zitstif-multibootmbr-usb-yumi or zitUSB for short (URL to download is toward the bottom of the post).
This flash drive image not only has multiple distros on it, but has an array of useful tools for any ‘hacker’, computer enthusiast, network admin, technician, etc. Here is the root of the flash drive: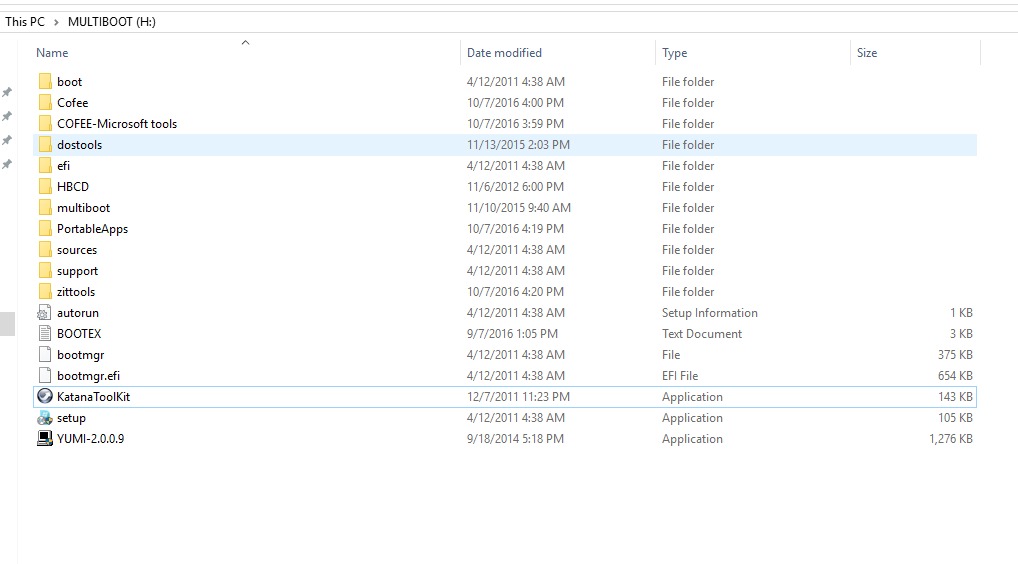
For those of you willing to look at the `tree` of this drive, here you go: http://zitstif.no-ip.org/usb/tree.txt
Here’s a list of the distros/bootable OSes:
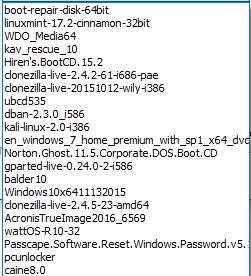
For clarification: WDO is Windows Defender Offline, kav_rescue is kaspersky AV live CD, the Windows 7 Home Premium is basically any version of Windows 7 (via a method like this), and there’s multiple versions of Clonezilla because I have ran into compatibility issues with certain systems.
TAKE NOTE THAT YUMI-2.0.0.9 IS ON THE ROOT OF THE DRIVE, USE THIS VERSION FOR ADDING OR REMOVING DISTROS! IF YOU USE ANY VERSION DIFFERENT TO ADD OR REMOVE DISTROS, YOU WILL POTENTIALLY MAKE YOUR FLASH DRIVE UNBOOTABLE!
I made an image of my flash drive using clone-zilla-2.4.2-61-i686-pae, however that version or any newer version should work in creating your flash drive.
A quick side note: I was able to boot off of this drive using a Macbook (13-inch, Late 2009). I first had to use Plop and then told the Macbook to boot off of USB. However, in the Yumi menu, the keyboard did not work and I had to use an external keyboard.
Requirements:
- 1 Flash drive that is 32GB or larger
- A computer with working USB ports
- clone-zilla-2.4.2-61-i686-pae or
newer and know-how for using clonezilla to restore an image (look here if needed)
#Update 8/30/2018, I’ve had problems using newer versions of clonezilla restoring this image to flash drives, so far it seems that clone-zilla-2.4.2-61-i686-pae will restore the image without any problems, it can be downloaded here: https://sourceforge.net/projects/clonezilla/files/clonezilla_live_stable/2.4.2-61/
- patience to download an 18GB file
- To use: a computer that supports CSM or legacy mode, system must also be x86 or x64, ARM is NOT SUPPORTED
Hashes:
zitstif-multibootmbr-usb-yumi-2.0.0.9-2017-07-11-19-img.rar
MD5: 0988fb81652742a595748ac723c8a787
SHA-1: 8adeb884baeff97a5c09721ae64ff6a5d88a96df
RAR content hashes (MD5):
ffe3d783099ca73716e2b640bfd831e7 blkdev.list
40bab056938e4c10321a605a093b32a6 blkid.list
e78a6e82dfbcd592ec3f3cac3845a734 dev-fs.list
ff0a4ce532aa9be376f4e49bc35fe572 sdd-pt.sf
d9aecb1e6f8b6be75219b313998ec8e0 sdd-chs.sf
890485aa018405d04fadcd3a51d71fd4 sdd-pt.parted
0989aa9d66fe2fbade298f8c6f1236db sdd-pt.parted.compact
ed356b009be474fef10efc60939de511 sdd-hidden-data-after-mbr
e2dbab6ba17e25d3ff12a179da13732e sdd-mbr
f0873661b3057fc74d65acaaf063ac64 sdd1.vfat-ptcl-img.gz.aa
b0bcbb15f49c38e2deaf9087bc2da5b0 sdd1.vfat-ptcl-img.gz.ab
0ebfd956346a0c1c6d72a1d385ef3b7a sdd1.vfat-ptcl-img.gz.ac
009174f7ddcc057f49e9dfc54da58d91 sdd1.vfat-ptcl-img.gz.ad
b303b75755c0815bbdcc69cb09540dfd sdd1.vfat-ptcl-img.gz.ae
7a466b46e75d7f2e58580a937b9fff74 info-lshw.txt
8eab9cdcaa09d256b20084b2e8839e15 info-dmi.txt
bdf55074c4e8720d2fa7c0a3bca7909b info-lspci.txt
4501bf778509426fba474f19fa0d0cf4 info-packages.txt
85396fcb9cb6ae3247dfdf0c34242ae4 parts
b1e4a422a5f04875f35577bf8856d688 disk
db0a67b885cff5a95ec3d745b0b33294 info-saved-by-cmd.txt
c5c44e45b2eed964753fbb6060caba23 clonezilla-img
Download:
File is hosted on Google Drive and MEGA.NZ. The URLs are available in a TXT file: http://zitstif.no-ip.org/usb/url.txt
sha1sum 654fc8f2d47ac3c4b8e31103ef819222f910a87e url.txt
Feel free to leave any feedback.
#10/15/2017 Recently a friend wanted me to make a copy for him. The USB drive I used to create the Clonezilla image, calls for a 32.1GB flash drive, however his flash drive is only 32GB. This is no issue. The zitUSB volume has about 10GB free and you can use the ‘expert’ option in Clonezilla, switch on the -icds flag, and lastly set the option for proportional partitions.
#8/3/2017 Due to limitations of MEGA.NZ, I have the file also hosted on Google Drive.
#7/22/2017 Currently trying to find another hoster outside of MEGA.NZ because MEGA.NZ limits how much you download at a time. (After downloading about 5GB, you have to wait about 5 hours until you can download more or you have to pay for a premium account. I’m currently looking into archive.org but I’m running into issues.)

