Recently I wanted to test Meraki’s ‘Threat Protection’ system and see if it was really up to snuff. First, I setup an up to date Windows 10 virtual machine where I disabled the anti-virus on this system. In this environment there isn’t any SSL inspection being done by Meraki and to my understanding, Cisco really doesn’t advocate using SSL inspection through Meraki. In my opinion, you are already at kind of a disadvantage with the lack of SSL inspection because most threats that need to be seriously considered will use encryption for evasion. Metasploit’s meterpreter payload has supported SSL and encryption for years. Plus you can setup legit certs for free if needed.
With that being said, I thought I would throw a softball at Meraki and see if it would do some sort of detection via HTTP. I tried downloading the benign eicar test file over HTTP and Meraki blocked it: ![]()
However, if you download the same file over HTTPS, Meraki does not block it (no surprise there). I then decided to step my game up and generate a payload using msfvenom and host it on a python3 http server ( python3 -m http.server ):
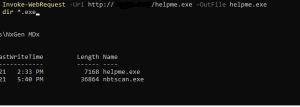
I was able to download the payload using powershell on the victim VM:
I was then able to run the payload on the victim system and have a session:
Meraki did not detect the payload or the session.. and here’s the the virustotal report for this payload:
This payload was not made in really any special way… it’s a pretty standard payload that I believe ALL IDS/IPS systems should be able to detect or block. However, I will give credit where credit is due. Later on I did receive an alert that this payload had slipped through:
Additionally, this Meraki configuration does not have Cisco’s Umbrella integrated yet. Would Umbrella have blocked it? I honestly don’t know but what I’m willing to test it.
I would like to add that a majority of events that I’ve seen under Security Center have been false positives. There is already enough noise in terms of information pertaining to networks. Meraki generating this just adds more unnecessary noise and can hamper investigations in my humble opinion.
I’m still thoroughly disappointed with this discovery because people are paying Cisco a lot of money for a false sense of security. Meraki should have blocked this threat right away. In the end of the day, I believe having well trained employees and thorough AV/EDR systems on endpoints is what matters most.
#Update 12/24/2021
I have setup the Umbrella client on the victim VM. Meraki blocked the known helpme.exe file, however if you simply use the shikata_ga_nai encoder to make a new file called helpme2.exe, this payload slipped through Meraki and Umbrella.
Here is the virustotal.com report for the file:
https://www.virustotal.com/gui/file/19cf577ac24452bfb715f421a6bdabadd0f2d043f60cbbf600e44e34dc14738f
I feel like I can confidentially say that Meraki/Umbrella security are a joke.