Dabbling about with the command line one day, I thought to myself, “Can’t I append text to a picture and be able, at a later time, read the text from the image?”.
By simply just using ‘>>‘, under Windows and Linux, you can append text to a picture file (like a jpeg for example). Bear in mind that this does change the hash sum of the file. Lastly, I’ve only tested this with jpeg images.
Here’s an example:
We have a file called ‘linux.jpg’ from, http://www.bose.res.in/~kapil/linux.jpg
By simply invoking:
echo "Secret Message: toor" >> linux.jpg
To find our “Secret Message”, simply invoke the follow:
egrep -a 'Secret' linux.jpg
If you’re using ‘xterm’, your output may look like this:
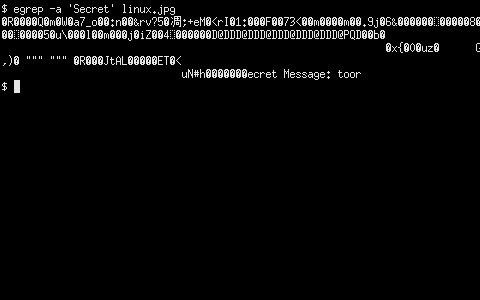
However, if you’re using something else and your output ‘borks’ your terminal and the output looks completely alien, use the reset command.
You can also do this in Windows as well, but the command would look like this:
type linux.jpg | findstr "Secret"
