Those of us who understand some of the great weaknesses in IPv4, know that under certain circumstances (especially in local area networks), attackers can carry out some pretty devious tasks. Arp-spoofing (http://en.wikipedia.org/wiki/ARP_spoofing) can be used to intercept traffic and even modify it accordingly to the attacker’s will. Programs like arpspoof, cain&abel, and especially ettercap-ng, when abused, can be used for purloining credentials and potentially identities.
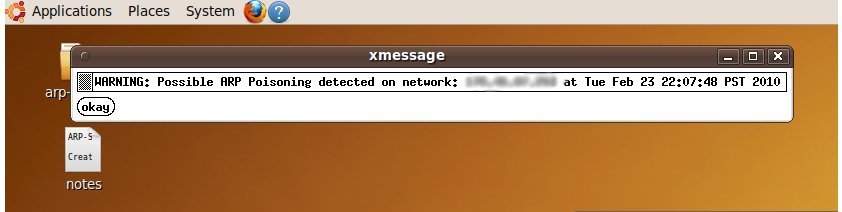
With this being true, I decided to write an implementation of a arp-spoofing detection program that is geared toward Ubuntu/Debian. The beauty of this program, is that instead of just creating logs that non-tech savvy users would most likely not glance at, this program alerts the end user via x-message. Granted, this x-message window can potentially get annoying, however this was intended. The end user needs to be alerted of if arp-spoofing is taking place, their information could be potentially at great risk.
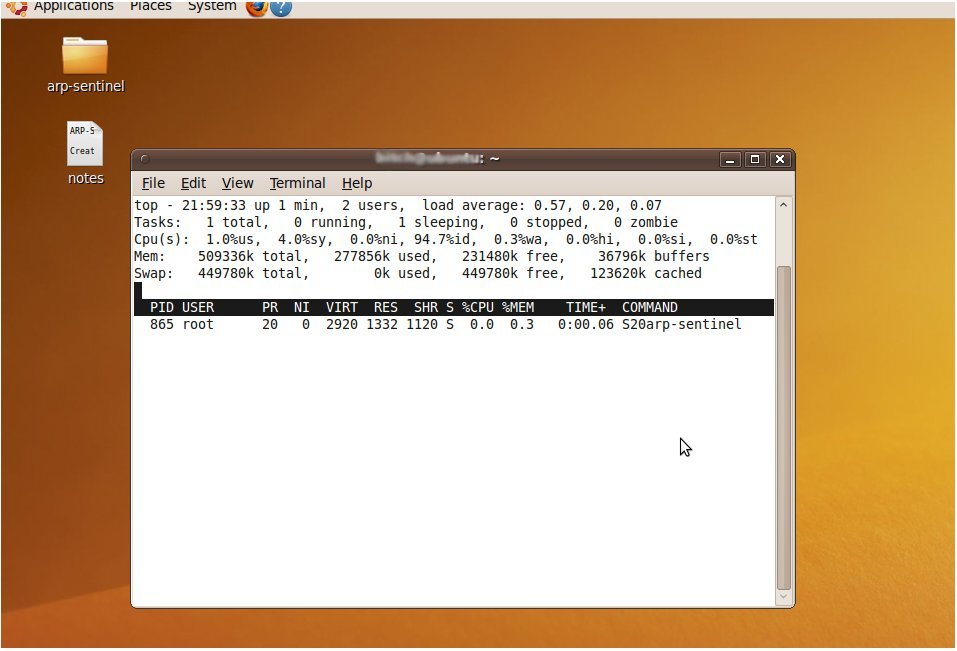
The beauty behind arp-sentinel, is that it uses very low resources and is mainly intended for end users who run Ubuntu on a laptop, who use insecure hotspots for whatever purposes. Here’s a screen shot of ‘top’ being used under Ubuntu 9.10 on a virtual machine:
Nifty eh? Here’s also a screen shot of the warning message that is displayed:
Here’s the program in a tar file:
http://zitstif.no-ip.org/arp-sent/arp-sentinel.tar
MD5sum: 79c54891a7b235bf6a2f5d4c779771c3
Tested to work on Ubuntu 9.10.