If you’ve worked in IT and have inherited other systems and networks to manage, you can definitely relate to having to work with situations that are less than ideal. Best practices can’t always be followed due to various reasons. (One main reason seems to be money related.) I am currently working with a client that has on-premise servers that are all bare metal and under-specced. We are in the process gathering information on their current setup and plan to decommission and consolidate their on-premise servers, and push them to use Office 365 instead.
I hope this post helps someone because I was having next to no luck being able to access the Exchange Management Shell. Oddly, the GUI tool worked fine, but I wanted to run powershell scripts to generate reports on the current configuration of the said Exchange server. Clicking on the powershell management shell for Exchange icon would result in:
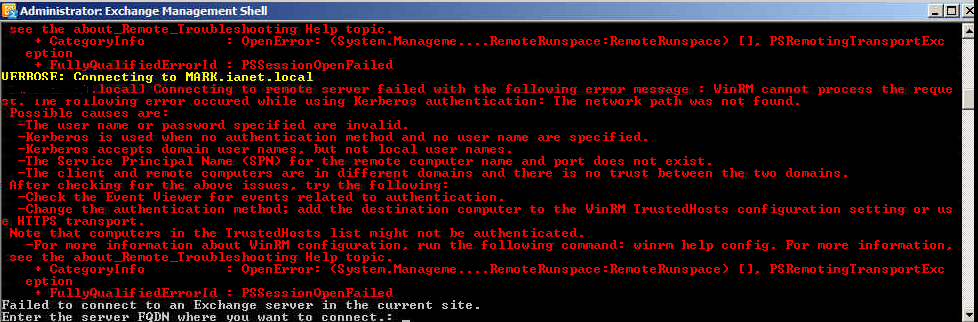
I troubleshooted all the suggested steps suggested in the error output and everything appeared to check out fine. I then just tried using a standard powershell prompt to try to authenticate to the local exchange powershell, and started getting errors like:
[ExchServer] Connecting to remote server failed with the following error message : The WinRM client received an HTTP status code of 403 from the remote WS-Management service. For more information, see the about_Remote_Troubleshooting Help topic. + CategoryInfo : OpenError: (System.Manageme….RemoteRunspace:RemoteRunspace) [], PSRemotingTransportExc eption + FullyQualifiedErrorId : PSSessionOpenFailed
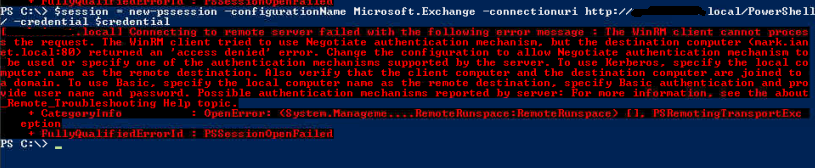
I found it curious that I was starting to get different error messages and felt like I was starting to get closer to being able to authenticate. What ended up working for me was to issue this command:
$session = new-pssession -configurationName Microsoft.Exchange -connectionuri http://change.me.local/PowerShell/ -Authentication Kerberos -credential $credential
You are then prompted with a gui logon prompt. Make sure to use Domain\UserName in the username field then use the proper password. Lo and behold, no errors were given and it looks like I was authenticated! To import the exchange powershell modules, issue this command:
Add-PSSnapin Microsoft.Exchange.Management.PowerShell.E2010;
Again, I really hope this helps save someone a headache and time. As for the root of what’s causing the powershell management shell for Exchange icon shortcut to fail, I’m not clear. So at this point this is just a workaround.

