Category Archives: Code
Code of course.
Testing for existence of programs via bash
For those of you who are into shell scripting, and want to know what in my opinion is the best way to test for whether programs exist or not, pay close attention.
In my humble opinion, the best way to test for the existence of a program, is to test the exit code of the previous command in an if loop.
Firstly, if you run a command that doesn’t exist, the exit code will always be ‘127′. If you don’t want to see the output of the command while testing for it, then just simply redirect all the output to /dev/null .
idontexist &> /dev/null
echo $?
127
Now, a friend suggested using this method for testing for programs in bash:
idontexist &> /dev/null || echo "You don't have 'idontexist'"; exit 1;
There are a few qualms with this. Firstly, depending on the program, if the program does not exit with the exit code of ‘0’, your shell script will then state ‘You don’t have ‘idontexist’ and then exit. However, you might actually have the program! Some programs exit with non-zero exit codes if you pass no arguments to them or even if you pass a ‘-h’ for a help argument to it. Also, since the echo statement is being terminated via the semicolon, ‘exit’ will then be executed. Ergo, this method looks great for just being a one liner, but if I want to test for the existence of a program, and if it doesn’t exist, and then exit with an error message displayed to the user, I highly suggest my following method:
idontexist &> /dev/null;
if [[ "$?" == "127" ]];
then
echo "'idontexist' appears to not be installed, check your PATH variable"; exit 1;
fi
More to come…
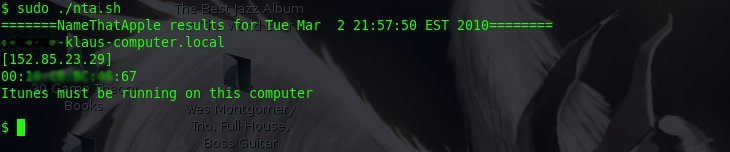
NameThatApple –nta.sh
There’s something about Apple computers that I like to pick on. It’s not really the computers per se, it’s mostly the end users who can get on my nerves. Most people who I’ve met that use Apple computers, have little to no knowledge about computers or information technology. Yet, at times, these people tend to get lofty because they use Apple Computers and feel as if they can be be smug towards you since you might not own an over priced PC. (An Apple computer, which I’ll explain).
Now, not all Apple computer users are this way, and I actually have a few friends who are huge computer enthusiasts, whom use Apple computers and are very knowledgeable in the field of information technology. Also, don’t mind if I meander, but if an Apple computer is a ‘computer’ and if you consider it personal to you.. then isn’t it technically a ‘PC’. as in personal computer? 🙂
With that aside, I’m reintroducing a bash shell script that one can use in a LAN to identify Apple computer users. I’ve tested it on Ubuntu and Backtrack and have had great results. As a matter of fact, a while ago I wrote this program, but as times have changed and the output of nmap has changed, I needed to rewrite this shell script.
Features of NameThatApple (nta):
Information discovery — finding the names of Apple computers which 90% of the time have their real name in the title.
Port scanning — this does a limited number of port scans on ports that are usually open on Apple computers
Iphone/Ipod touch jail break test — If port 22 is discovered, a python script relying on pexpect will test to see if the default password for the root account is ‘alpine’.
MAC address discovery — nta will ARP the Apple computer and report back the MAC address.
If you have problems resolving the host names of the Apple comptuers with my program, make sure your Linux distro supports MDNS and/or you may have to try a different version of netcat.
If you have any other problems, please contact me or leave a comment.
Here’s some screen shots of nta.sh in action: (Note: I blurred the end users names out for privacy)
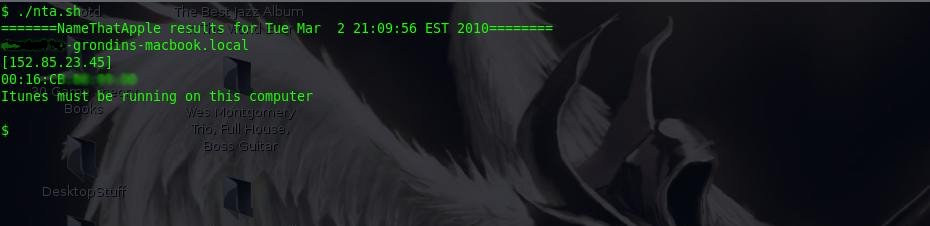
If you want to capture the out put of nta.sh, then pipe the output to ‘tee’, like this:
sudo ./nta.sh | tee newlog.log
Here are the files:
Plain text (main shell script):
http://zitstif.no-ip.org/nta/nta.txt
Plain text (jail break test script):
http://zitstif.no-ip.org/nta/jailbreaktest.txt
Tar file (both files):
http://zitstif.no-ip.org/nta/nta.tar
MD5sum: 0e4672083861d00893afa9d9f0527574
As always, more to come! I’m planning on adding more features to nta.sh, such as having it interface through some means with metasploit.
arp-sentinel
Those of us who understand some of the great weaknesses in IPv4, know that under certain circumstances (especially in local area networks), attackers can carry out some pretty devious tasks. Arp-spoofing (http://en.wikipedia.org/wiki/ARP_spoofing) can be used to intercept traffic and even modify it accordingly to the attacker’s will. Programs like arpspoof, cain&abel, and especially ettercap-ng, when abused, can be used for purloining credentials and potentially identities.
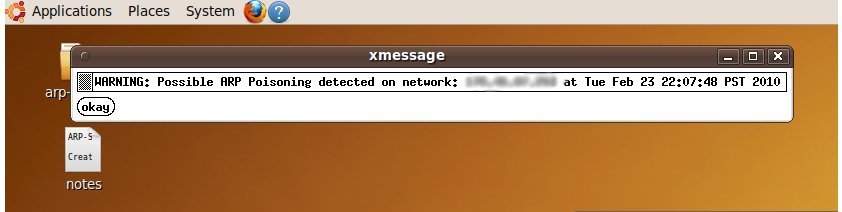
With this being true, I decided to write an implementation of a arp-spoofing detection program that is geared toward Ubuntu/Debian. The beauty of this program, is that instead of just creating logs that non-tech savvy users would most likely not glance at, this program alerts the end user via x-message. Granted, this x-message window can potentially get annoying, however this was intended. The end user needs to be alerted of if arp-spoofing is taking place, their information could be potentially at great risk.
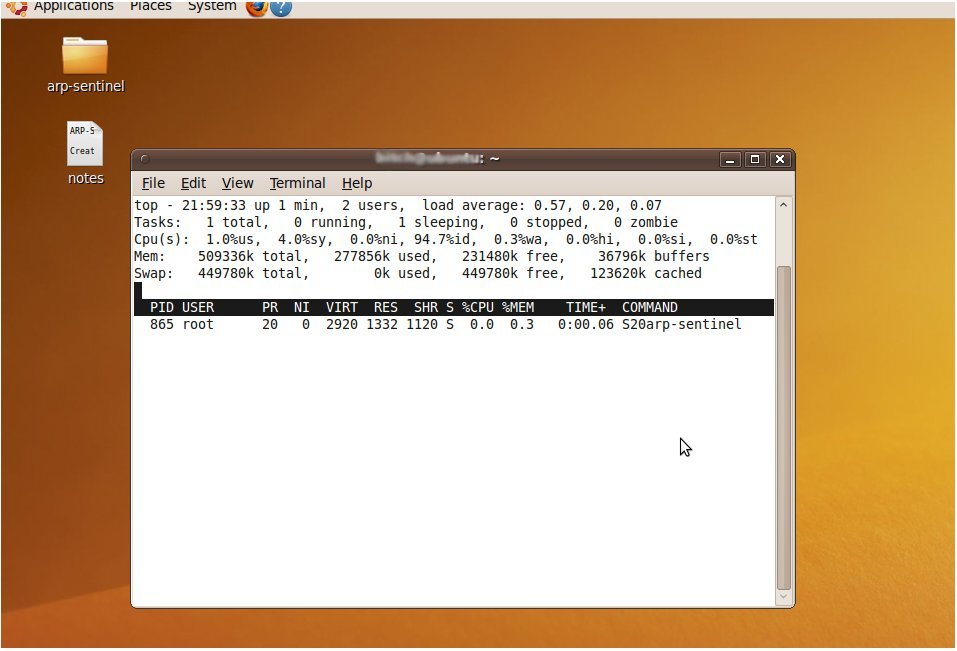
The beauty behind arp-sentinel, is that it uses very low resources and is mainly intended for end users who run Ubuntu on a laptop, who use insecure hotspots for whatever purposes. Here’s a screen shot of ‘top’ being used under Ubuntu 9.10 on a virtual machine:
Nifty eh? Here’s also a screen shot of the warning message that is displayed:
Here’s the program in a tar file:
http://zitstif.no-ip.org/arp-sent/arp-sentinel.tar
MD5sum: 79c54891a7b235bf6a2f5d4c779771c3
Tested to work on Ubuntu 9.10.
HEAD requests on multiple web servers, all with a one liner
If you need a quick way of getting server versions and you want to do this with a one liner here’s your solution:
for i in $(cat websites); do printf "HEAD / HTTP1/.0\n\r\n" | nc -vv ${i} 80; done
‘websites’, would be a file that contains a list of websites either by domain names or IP addresses. You could also enumerate an array of websites for cases where you have stored output into an array. i.e.
array=($(cat /var/log/apache2/access.log | awk '{print $1}' | sort | uniq));
for i in ${array[@]}; do printf "HEAD / HTTP/1.0\n\r\n" | nc -vv ${i} 80; done
Lastly, a while back, I wrote a python script that does pretty much the same thing:
Plain text:
http://zitstif.no-ip.org/webEnum.txt
tar archive:
http://zitstif.no-ip.org/webEnum.tar
MD5sum: dcb02fff9e69fb004c8e6456ed82c424