All posts by zitstif
Testing for existence of programs via bash
For those of you who are into shell scripting, and want to know what in my opinion is the best way to test for whether programs exist or not, pay close attention.
In my humble opinion, the best way to test for the existence of a program, is to test the exit code of the previous command in an if loop.
Firstly, if you run a command that doesn’t exist, the exit code will always be ‘127′. If you don’t want to see the output of the command while testing for it, then just simply redirect all the output to /dev/null .
idontexist &> /dev/null
echo $?
127
Now, a friend suggested using this method for testing for programs in bash:
idontexist &> /dev/null || echo "You don't have 'idontexist'"; exit 1;
There are a few qualms with this. Firstly, depending on the program, if the program does not exit with the exit code of ‘0’, your shell script will then state ‘You don’t have ‘idontexist’ and then exit. However, you might actually have the program! Some programs exit with non-zero exit codes if you pass no arguments to them or even if you pass a ‘-h’ for a help argument to it. Also, since the echo statement is being terminated via the semicolon, ‘exit’ will then be executed. Ergo, this method looks great for just being a one liner, but if I want to test for the existence of a program, and if it doesn’t exist, and then exit with an error message displayed to the user, I highly suggest my following method:
idontexist &> /dev/null;
if [[ "$?" == "127" ]];
then
echo "'idontexist' appears to not be installed, check your PATH variable"; exit 1;
fi
More to come…
Why wireless networks can be an anathema towards security..
Xplico Part 1:
Xplico Part 2:
http://www.securitytube.net/Xplico-Network-Forensic-Analysis-Tool-Demo-video.aspx
If you’re curious about a good live Linux forensics distro that even includes this tool, check out:
http://www.deftlinux.net/
NameThatApple –nta.sh
There’s something about Apple computers that I like to pick on. It’s not really the computers per se, it’s mostly the end users who can get on my nerves. Most people who I’ve met that use Apple computers, have little to no knowledge about computers or information technology. Yet, at times, these people tend to get lofty because they use Apple Computers and feel as if they can be be smug towards you since you might not own an over priced PC. (An Apple computer, which I’ll explain).
Now, not all Apple computer users are this way, and I actually have a few friends who are huge computer enthusiasts, whom use Apple computers and are very knowledgeable in the field of information technology. Also, don’t mind if I meander, but if an Apple computer is a ‘computer’ and if you consider it personal to you.. then isn’t it technically a ‘PC’. as in personal computer? 🙂
With that aside, I’m reintroducing a bash shell script that one can use in a LAN to identify Apple computer users. I’ve tested it on Ubuntu and Backtrack and have had great results. As a matter of fact, a while ago I wrote this program, but as times have changed and the output of nmap has changed, I needed to rewrite this shell script.
Features of NameThatApple (nta):
Information discovery — finding the names of Apple computers which 90% of the time have their real name in the title.
Port scanning — this does a limited number of port scans on ports that are usually open on Apple computers
Iphone/Ipod touch jail break test — If port 22 is discovered, a python script relying on pexpect will test to see if the default password for the root account is ‘alpine’.
MAC address discovery — nta will ARP the Apple computer and report back the MAC address.
If you have problems resolving the host names of the Apple comptuers with my program, make sure your Linux distro supports MDNS and/or you may have to try a different version of netcat.
If you have any other problems, please contact me or leave a comment.
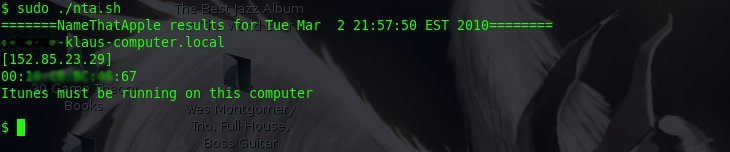
Here’s some screen shots of nta.sh in action: (Note: I blurred the end users names out for privacy)
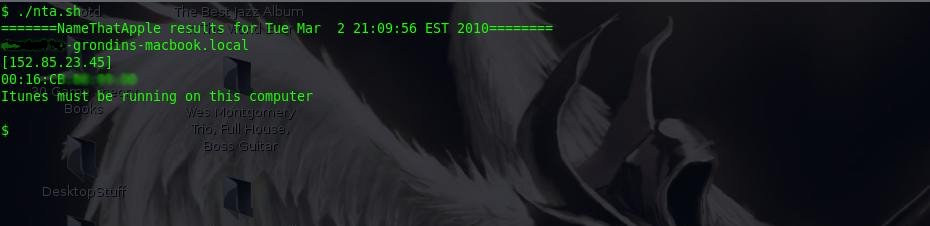
If you want to capture the out put of nta.sh, then pipe the output to ‘tee’, like this:
sudo ./nta.sh | tee newlog.log
Here are the files:
Plain text (main shell script):
http://zitstif.no-ip.org/nta/nta.txt
Plain text (jail break test script):
http://zitstif.no-ip.org/nta/jailbreaktest.txt
Tar file (both files):
http://zitstif.no-ip.org/nta/nta.tar
MD5sum: 0e4672083861d00893afa9d9f0527574
As always, more to come! I’m planning on adding more features to nta.sh, such as having it interface through some means with metasploit.
Protecting end users by black listing domain names
One of the many programs that I use for Windows to help prevent and remove malware is SpyBot S&D. One of the methods that SpyBot S&D utilizes, is by editing the hosts file, which for Windows is located at (usually):
C:\WINDOWS\system32\drivers\etc\hosts
About a year ago, I was monkeying around with my hosts file and noticed all the entries put by SpyBot S&D. I thought to myself, “What a wonderful idea.” For those of you who aren’t familiar with the hosts file, please take a gander at this:
http://en.wikipedia.org/wiki/Hosts_file
Ergo, I compiled (well I used quite a bit of from the hosts file that was edited under Windows by SpyBot S&D)a list of offending domains that are usually associated with scams, malware, and/or other nefarious things and put it on my website. I felt that end users who use Linux or even Mac OS X could benefit from editing their hosts file in such a way. Here’s the hosts file:
http://zitstif.no-ip.org/THELIST.txt
MD5sum: 7ec6a57b82d53359c3bcff54d0b1cc62
For *nix end users, if you want to append THELIST.txt on the fly over the Internet via bash shell, give this a try and verify your results as root:
printf "GET /THELIST.txt HTTP/1.0\n\r\n" | nc -vv zitstif.no-ip.org 80 2>&1 | egrep -v 'HTTP|Apache|Date:|ETag:|Accept-Ranges:|Content-|Connection:|Modified:|Connection' >> /etc/hosts
By doing this, you’ll protect your end users by making the blacklisted domain names unavailable to them. This may not be perfect, but this is one of the many ways you can help prevent identity theft for your end users or even yourself.
More to come.